In order to get started with the Athena Templates, an IAM user with the required AWS permissions and programmatic access is required.
Additionally, you may need to ensure that Platform IP Addresses are whitelisted
Steps
-
Login to your AWS Management Console
-
Search for and go to the IAM service page
-
Select "Policies" on the left sidebar
-
Click the blue "Create policy" button
-
Select the "Visual editor" tab
-
Add required Athena permissions
a. On the "Service" dropdown, search for and select "Athena"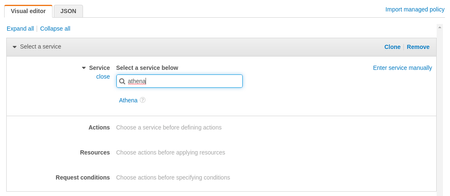b. On the "Actions" dropdown
i. Under "Read" select "GetQueryExecution"
ii. Under "Write" select "StartQueryExecution"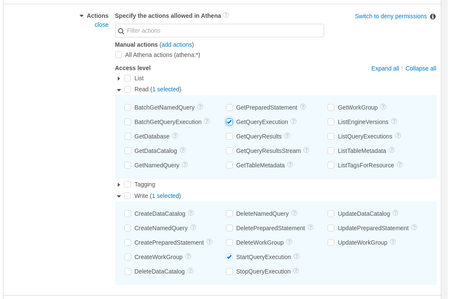c. On the "Resources" dropdown, click "Add ARN"
i. Add your region ID and workgroup name or select "Any" for both options - this example, the region has been set to"*"and the workgroup set to"primary"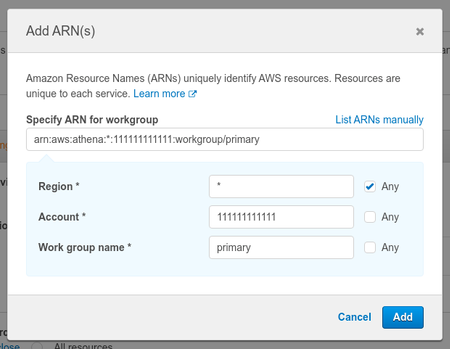d. Skip the "Request Conditions" dropdown
e. Click "Add additional permissions" to add the next set of permissions -
Add required S3 permissions (several separate groups are needed for S3)
a. On the "Service" dropdown, search for and select "S3"
b. On the "Actions" dropdown
i. Under "List" select "ListBucket"
c. On the "Resources" dropdown, click "Add ARN"
i. Add a bucket for source data in our example the bucket is "shipyard-athena-demo"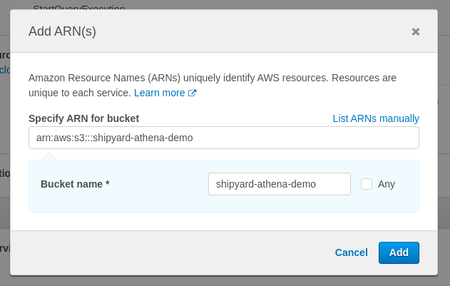d. Skip the "Request Conditions" dropdown
e. Click "Add additional permissions" to add the next set of permissions -
Add required S3 permissions (several separate groups are needed for S3)
a. On the "Service" dropdown, search for and select "S3"
b. On the "Actions" dropdown
i. Under "Read" select "GetObject"
c. On the "Resources" dropdown, click "Add ARN"
i. Add a bucket location for source data in our example we're using the "shipyard-athena-demo" bucket with an optional "data" folder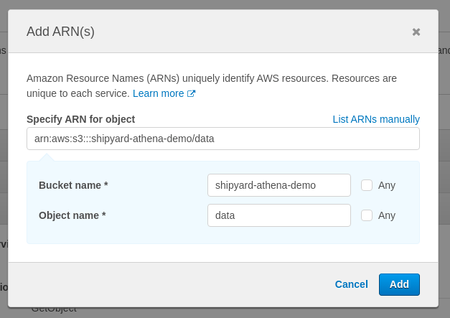d. Skip the "Request Conditions" dropdown
e. Click "Add additional permissions" to add the next set of permissions -
Add required S3 permissions (several separate groups are needed for S3)
a. On the "Service" dropdown, search for and select "S3"
b. On the "Actions" dropdown
i. Under "List" select "ListBucket", "ListBucketMultipartUploads", and "ListMultipartUploadParts"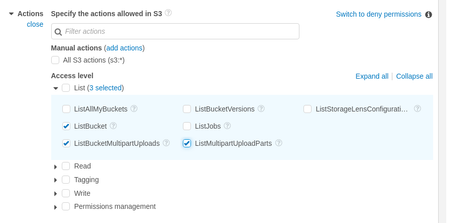 ii. Under "Get" select "GetObject" and "GetBucketLocation"  iii. Under "Write" select "AbortMultipartUpload" and "PutObject" 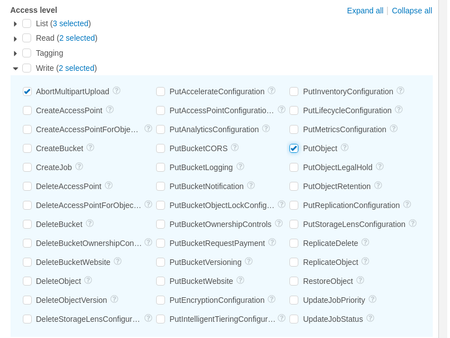c. On the "Resources" dropdown, click "Add ARN"
i. Add bucket location and optional folder example "shipyard-athena-demo" and "logs"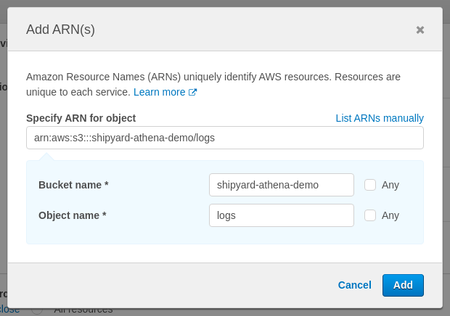d. Skip the "Request Conditions" dropdown
e. Click "Add additional permissions" to add the next set of permissions -
Add required Glue permissions
a. On the "Service" dropdown, search for and select "Glue"
b. On the "Actions" dropdown
i. Under "Read" select "GetTable"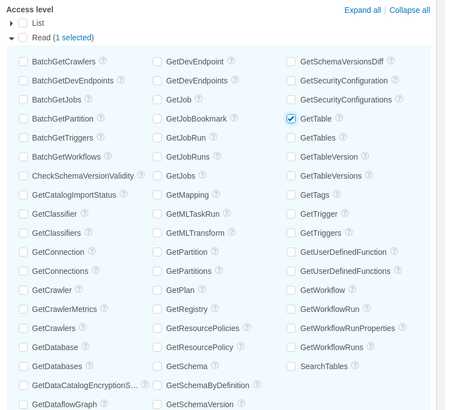c. On the "Resources" dropdown, click "Add ARN" i. Select "Any in this account" or add specific catalog, database, and table values - in our example we use "Any in this account" for all three (the "Any in this account" has not been selected since this overrides the example account ID with the Platform account ID)
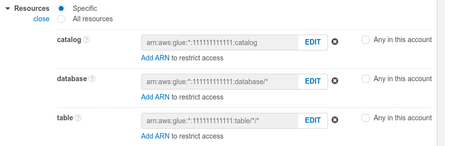d. Skip the "Request Conditions" dropdown
-
Click "Next: Tags"
-
Click "Next: Review"
-
Add policy name
-
Click "Create policy"
-
Attach to an IAM User with programmatic access
-
Add the IAM user's access key ID and secret access key into the corresponding fields on the Blueprint
i. These values can be generated for any IAM User with programmatic access in the "Users" page
Notes
-
AWS resource on IAM and Athena
-
Example IAM policy
-
Full IAM JSON using example values (from the steps outlined in the previous section)
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"athena:StartQueryExecution",
"athena:GetQueryExecution",
"s3:ListBucket",
"glue:GetTable"
],
"Resource": [
"arn:aws:athena:*:111111111111:workgroup/primary",
"arn:aws:s3:::shipyard-athena-demo",
"arn:aws:glue:*:111111111111:catalog",
"arn:aws:glue:*:111111111111:table/*/*",
"arn:aws:glue:*:111111111111:database/*"
]
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::shipyard-athena-demo/data"
},
{
"Sid": "VisualEditor2",
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:ListBucketMultipartUploads",
"s3:AbortMultipartUpload",
"s3:ListBucket",
"s3:GetBucketLocation",
"s3:ListMultipartUploadParts"
],
"Resource": [
"arn:aws:s3:::shipyard-athena-demo/logs",
"arn:aws:s3:::shipyard-athena-demo"
]
}
]
}